This is the latest Cisco 350-701 scor dumps

Keep it simple, I just want to simply express what I posted today!
Below I will share 350-701 scor dumps, free online practice questions, and exam PDF. All content comes from leads4pass 350-701 Dump and share!
The latest and complete Cisco 350-701 exam in November has 359 questions and answers. We shared 13 questions for free, you can test online first. You can also directly enter the leads4pass 350-701 channel https://www.leads4pass.com/350-701.html. It is guaranteed to pass the exam 100% successfully.
Cisco 350-701 Online Practice Test
Verify the results at the end of the article
QUESTION 1
What is the primary benefit of deploying an ESA in hybrid mode?
A. You can fine-tune its settings to provide the optimum balance between security and performance for your environment
B. It provides the lowest total cost of ownership by reducing the need for physical appliances
C. It provides maximum protection and control of outbound messages
D. It provides email security while supporting the transition to the cloud
Cisco Hybrid Email Security is a unique service offering that facilitates the deployment of your email security
infrastructure both on premises and in the cloud. You can change the number of on-premises versus cloudusers at any
time throughout the term of your contract, assuming the total number of users does not change.This allows for
deployment flexibility as your organization\\’s needs change.
QUESTION 2
Which two mechanisms are used to control phishing attacks? (Choose two)
A. Enable browser alerts for fraudulent websites.
B. Define security group memberships.
C. Revoke expired CRL of the websites.
D. Use antispyware software.
E. Implement email filtering techniques.
QUESTION 3
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
A. transparent
B. redirection
C. forward
D. proxy gateway
QUESTION 4
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be
added on the Cisco UC Manager platform?
A. Certificate Trust List
B. Endpoint Trust List
C. Enterprise Proxy Service
D. Secured Collaboration Proxy
QUESTION 5
Refer to the exhibit.
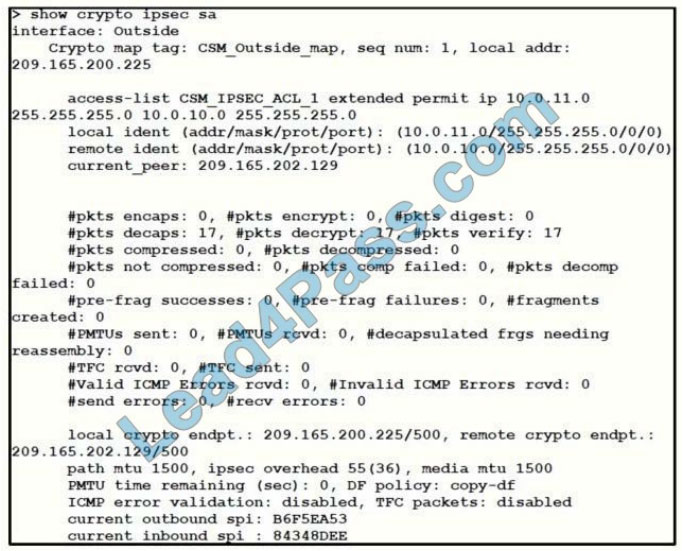
Traffic is not passing through IPsec site-to-site VPN on the Firepower Threat Defense appliance.
What is causing this issue?
A. No split-tunnel policy is defined on the Firepower Threat Defense appliance.
B. The access control policy is not allowing VPN traffic in.
C. Site-to-site VPN peers are using different encryption algorithms.
D. Site-to-site VPN preshared keys are mismatched.
QUESTION 6
What is managed by Cisco Security Manager?
A. access point
B. WSA
C. ASA
D. ESA
Reference: https://www.cisco.com/c/en/us/products/security/security-manager/index.html
QUESTION 7
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?
A. AMP
B. AnyConnect
C. DynDNS
D. Talos
When Umbrella receives a DNS request, it uses intelligence to determine if the request is safe, malicious or
risky–meaning the domain contains both malicious and legitimate content. Safe and malicious requests are routed as
usual or blocked, respectively. Risky requests are routed to our cloud-based proxy for deeper inspection. The Umbrella
proxy uses Cisco Talos web reputation and other third-party feeds to determine if a URL is malicious.
QUESTION 8
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode?
(Choose two)
A. When the Cisco WSA is running in transparent mode, it uses the WSA\\’s own IP address as the HTTP request
destination.
B. The Cisco WSA responds with its own IP address only if it is running in explicit mode.
C. The Cisco WSA is configured in a web browser only if it is running in transparent mode.
D. The Cisco WSA uses a Layer 3 device to redirect traffic only if it is running in transparent mode.
E. The Cisco WSA responds with its own IP address only if it is running in transparent mode.
The Cisco Web Security Appliance (WSA) includes a web proxy, a threat analytics engine, antimalware engine, policy
management, and reporting in a single physical or virtual appliance. The main use of the Cisco WSA is to protect users
from accessing malicious websites and being infected by malware.You can deploy the Cisco WSA in two different
modes:?Explicit forward mode?Transparent modeIn explicit forward mode, the client is configured to explicitly use the
proxy, subsequently sending all web traffic to the proxy. Because the client knows there is a proxy and sends all traffic
to the proxy in explicit forward mode, the client does not perform a DNS lookup of the domain before requesting the
URL. The Cisco WSA is responsible for DNS resolution, as well.
Reference: https://www.cisco.com/c/en/us/tech/content-networking/web-cache-communicationsprotocolwccp/index.html->Therefore answer D is correct as redirection can be done on Layer 3 device only.In transparent mode, the client is unaware its traffic is being sent to a proxy (Cisco WSA) and, as a result, the client uses DNS to resolve the domain name in the URL and send the web request destined for the web server (not the proxy). When you configure the Cisco WSA in transparent mode, you need to identify a network choke point with a redirection device (a Cisco ASA) to redirect traffic to the proxy.
WSA in Transparent modeReference: CCNP And CCIE Security Core SCOR 350-701 Official Cert Guide-> Therefore in
Transparent mode, WSA uses its own IP address to initiate a new connection the Web Server(in step 4 above)->
Answer E is correct.Answer C is surely not correct as WSA cannot be configured in a web browser in either
mode.Answer A seems to be correct but it is not. This answer is correct if it states “When the Cisco WSA is running
intransparent mode, it uses the WSA\\’s own IP address as the HTTP request source” (not destination).
QUESTION 9
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also provides an
option to specify HTTP/TFTP commands to perform file retrieval from the server?
A. url
B. terminal
C. profile
D. selfsigned
QUESTION 10
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements?
A. Cisco Umbrella
B. Cisco AMP
C. Cisco Stealthwatch
D. Cisco Tetration
QUESTION 11
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of
a network?
A. SDN controller and the cloud
B. management console and the SDN controller
C. management console and the cloud
D. SDN controller and the management solution
QUESTION 12
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
A. user input validation in a web page or web application
B. Linux and Windows operating systems
C. database
D. web page images
SQL injection usually occurs when you ask a user for input, like their username/userid, but the user gives(“injects”) you
an SQL statement that you will unknowingly run on your database. For example:Look at the following example, which
creates a SELECT statement by adding a variable (txtUserId) to a selectstring. The variable is fetched from user input
(getRequestString):txtUserId = getRequestString(“UserId”);txtSQL = “SELECT * FROM Users WHERE UserId = ” +
txtUserId;If user enter something like this: “100 OR 1=1” then the SQL statement will look like this:SELECT * FROM
Users WHERE UserId = 100 OR 1=1;The SQL above is valid and will return ALL rows from the “Users” table, since OR
1=1 is always TRUE. Ahacker might get access to all the user names and passwords in this database.
QUESTION 13
Refer to the exhibit. What does the number 15 represent in this configuration?

A. access list that identifies the SNMP devices that can access the router
B. interval in seconds between SNMPv3 authentication attempts
C. number of possible failed attempts until the SNMPv3 user is locked out
D. privilege level for an authorized user to this router
The syntax of this command is shown below: snmp-server group [group-name {v1 | v2c | v3 [auth | noauth | priv]}] [read
read-view] [ write write-view] [notify notify-view] [access access-list] The command above restricts which IP source
addresses are allowed to access SNMP functions on the router. You could restrict SNMP access by simply applying an
interface ACL to block incoming SNMP packets that don\\’t come from trusted servers. However, this would not be as
effective as using the global SNMP commands shown in this recipe. Because you can apply this method once for the
whole router, it is much simpler than applying ACLs to block SNMP on all interfaces separately. Also, using interface
ACLs would block not only SNMP packets intended for this router, but also may stop SNMP packets that just happened
to be passing through on their way to some other destination device.
Publish the answer:
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| D | AE | A | A | B | C | D | DE | C | D | D | A | B |
PS. Cisco 350-701 exam PDF
Google Drive: https://drive.google.com/file/d/1LVh707ZFnXXMXnWHSgYRDGhgicZHeNs1/view?usp=sharing
Thank you for reading! Keep things simple! Get the complete Cisco 350-701 exam questions and answers https://www.leads4pass.com/350-701.html. Guarantee the successful passing of the exam.
Like, please bookmark and share!

![[New May 2023] Updated 300-425 Dumps For 300-425 ENWLSD Exam](https://www.ciscoexampdf.com/wp-content/uploads/2023/05/Updated-300-425-Dumps.jpg)
